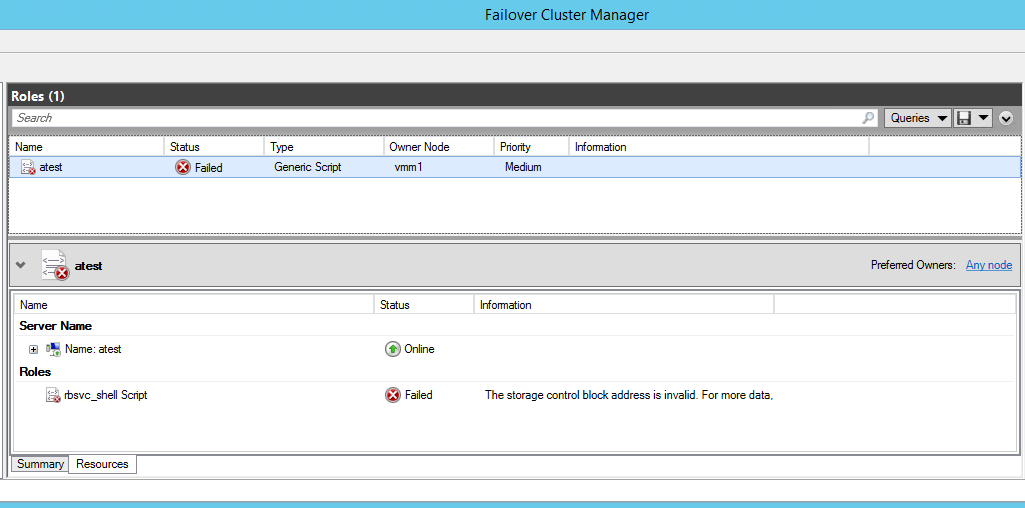
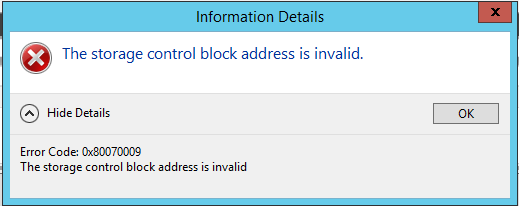
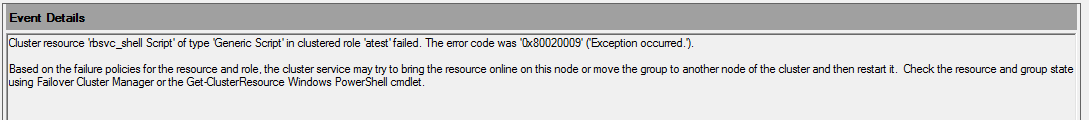
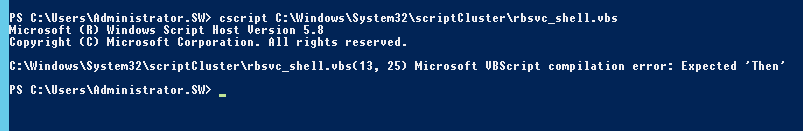
I would like to describe resolution of the problem with Terminal Services. When you are using Terminal Services in conjunction with License Server on separate machine, you may experience following symptoms:
- During the Logon Process, user receives the message “Access denied.”. It is shown instead logon screen, just after the “Welcome” message.
- Within application and system event logs, there is no related error messages.
- Within the TerminalServices-LocalSessionManager event log, there is following message correlated with user logon attempt: “Session X has been disconnected, reason code 12”, where X means number of logon session granted to user logon try by Session manager.
- This problem you may experience on Windows 2008 R2 as well on 2012 (R2).
- GPO policy update failure often occurs simultaneously.
Temporary solution to this problem may be modifying the following registry entry:
1 2 | HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\ IgnoreRegUserConfigErrors (DWORD) = 1 |
After addition of this registry value you need to reboot affected server.
After mitigation of poor user experience, you can peacefully start real diagnosis, what is wrong in your environment. In one of the cases, the real issue was mistake in windows firewall configuration of domain controlers, what was applied by GPO. In affecting GPO, there was rule denying “SMB over TCP” traffic.
It may be something different in your case, but always it must be something connect with domain controllers.